Working Remotely is the ‘New Normal’– How Can Cyber Insurance Help You?
In July, we all saw the ramifications of a well-performed hack. Twitter experienced the most catastrophic security breach in their company’s history. With Elon Musk, Barack Obama, Joe Biden, Bill Gates, and other high-profile Twitter users among the hacked users. This hack caused Twitter to shut down all blue-checked accounts. This breach of security cost Twitter users more than $118,000 and the company more in their reputation in just a few short hours.
With most of business and social interaction moving toward technology-centered avenues, this can be troubling for most business owners. What will your company do if this happens to you? Has the global pandemic and stay-at-home orders made you more vulnerable to potential cyber-attacks? How can you protect yourself and your company? Let’s explore!
Consider Investing in Cyber Insurance
Cyber insurance covers the expense incurred due to a data breach, virus, or other cyber-attacks and fraud. It can also cover legal claims that come from a security breach. As companies utilize cloud software, personal computers and laptops, and other technology-based means to store their sensitive data, their risk for a security breach becomes exponentially larger.
The Identity Theft Resource Center claims that in 2018 businesses experienced 571 breaches in security, which exposed 415 million employee and customer records.
When you do experience a breach as a company, federal law requires you to perform an extensive list of to-dos. If you have cyber insurance coverage, your carrier will take that responsibility on.
How has your Business Become More Vulnerable?
As businesses moved to a new work-from-home model, cyberattacks increased. With most company communication done through e-mail, Slack, or other online platforms, the risk of a breach exponentially increases. This could cause a company to experience massive monetary loss and reputation damage.
What are the signs you may be at risk of experiencing a cyber attack?
- You are receiving requests for transactions, like direct deposits or electronic fund transfers
- Unsolicited communications are coming through by unknown companies or people
- Links within the email do not match; check links by rolling your cursor over the link to see if the two match with the content and the email address.
- Requests with a high sense of urgency, asking you to complete documentation immediately.
- Requests for usernames and passwords, or other personal details like banking information.
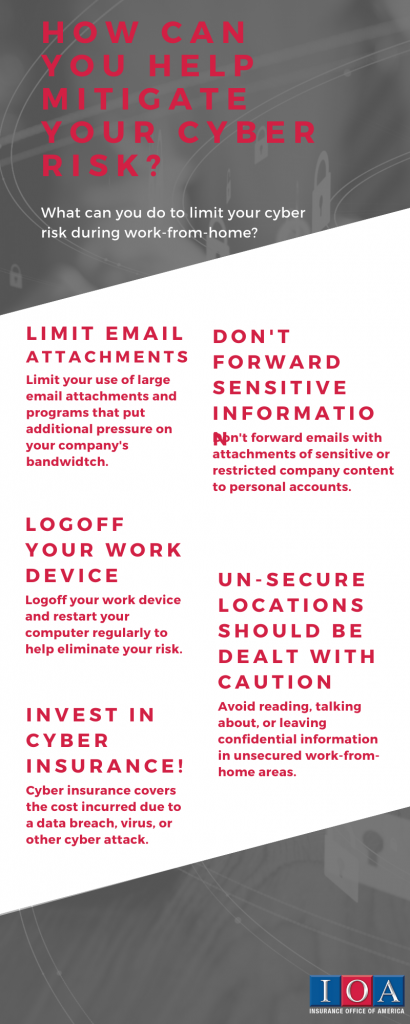
What can you do to help mitigate this risk?
- Limit your use of large email attachments and programs that put pressure on your company’s bandwidth ecosystems.
- Do not forward emails with attachments that contain highly restricted or company confidential information to personal accounts.
- Avoid reading, talking about, or leaving confidential information in unsecured work-from-home areas.
- Log-off of your work device when you’re not using it.
- Shred sensitive documents.
- Restart your computer regularly.
These tips along with the added security of cyber insurance should prepare your business for potential cybersecurity breaches. Learn more about how cyber insurance can help your company today. Contact us for more information.